Email providers use several mechanisms to safeguard against email spoofing, tampering, and phishing attacks. Three essential methods used for this purpose are SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
Email Sender Details
To understand how SPF, DKIM and DMARC work, we need to look at two parts of Email Senders:
- From: a ‘friendly’ name of the company sending the email
- Sender: the actual server or IP addresses that is sending
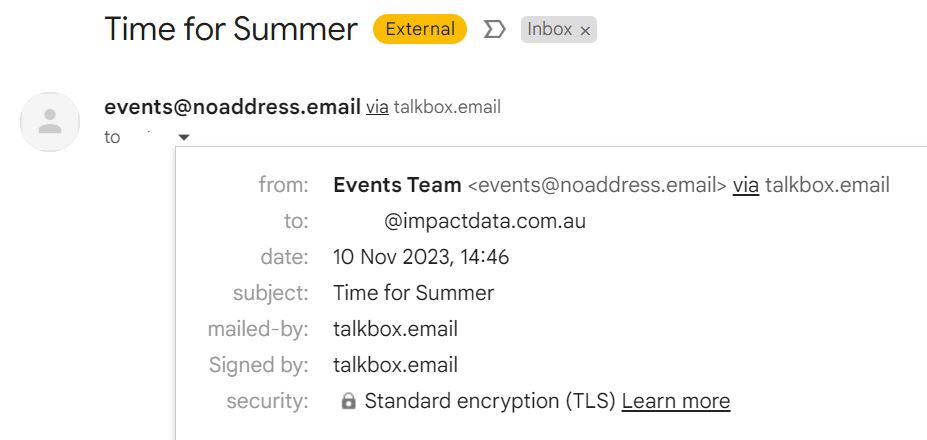
In this example,
- From: Events Team <events@noaddress.email>
- Sender: talkbox.email (“events=noaddress.email@talkbox.email”)
SPF (Sender Policy Framework)
What is SPF?
Sender Policy Framework (SPF) is an email authentication method designed to prevent email spoofing.
An SPF record will designate list of IP addresses that are permitted to send on your behalf; and operates by allowing the recipient’s email server to confirm whether the sender is authorized to send emails on behalf of the domain.
Why SPF Matters
Without an SPF record, when recipients receive your emails, their email providers may suspect that the sender’s email address is forged, potentially leading to your emails being marked as spam or even bounced by the recipient’s email provider.
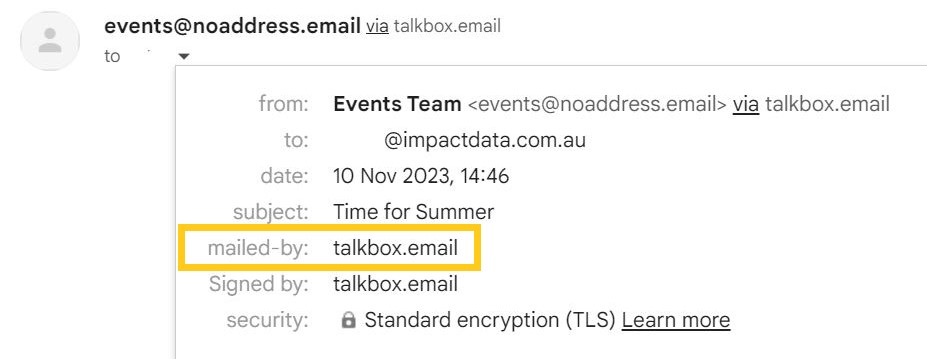
Referring to the email sender details: while the “From” address is “events@noaddress.email”, the “Sender” is TalkBox’s sending domain, which has its own SPF record.
DKIM (DomainKeys Identified Mail)
What is DKIM?
DomainKeys Identified Mail (DKIM) is another email authentication method that enhances email security. It involves adding a digital signature to the email’s header. This signature can be verified by the recipient’s email server. A valid signature confirms that the email hasn’t been altered during transit and truly originates from the claimed domain.
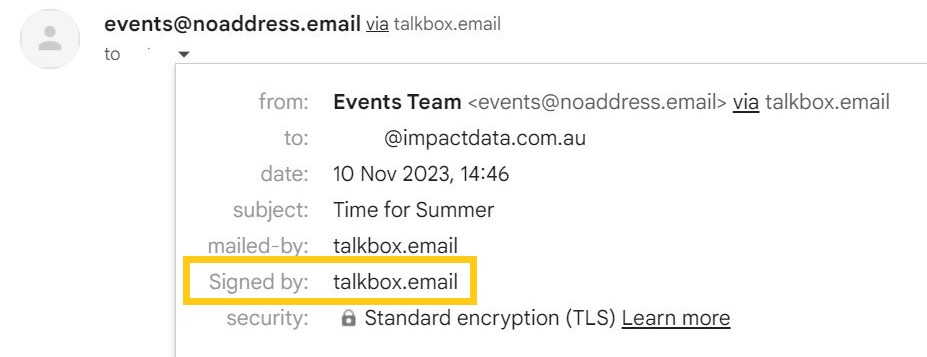
Referring to the example, the DKIM is the signature issued by talkbox.email
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
What is DMARC?
Domain-based Message Authentication, Reporting, and Conformance (DMARC) empowers domain owners to establish a policy for handling emails that fail SPF and DKIM checks. This policy can include rules like “quarantine” or “reject” for such emails, specifying how receiving email servers should treat them.
DMARC Example
For instance, your domain can set a “quarantine” policy. This means that emails failing SPF or DKIM checks will be considered suspicious and directed to the recipient’s spam or quarantine folder.
For example, the DMARC policy for talkbox.email includes a strict “reject” policy:
v=DMARC1; p=reject; rua=mailto:dmarc@impactdata.com.au
How DMARC can affect email delivery
There are two scenarios to consider when setting up your email senders in TalkBox.
- Your business domain does not have a strict DMARC policy
- Your business domain does have a strict DMARC policy, such as “reject”
In scenario 1, the domain in the “From” address is checked, and because it does not have a strict DMARC policy, it is effectively ignored when assessing the legitimacy of an email. The “Sender” controls the process, which means the SPF and DKIM of the “talkbox.email” domain confirm the email is legitimate.
In scenario 2, the domain in the “From” address is checked, and the DMARC policy will flag that the domain for both the “From” and “Sender” should be aligned. This means your business domain is warning against allowing “talkbox.email” to send emails. It does not automatically mean it will be rejected, but it will likely impact some recipients.
Recommendation
Leverage talkbox.email domain
You can choose to leverage the talkbox.email SPF, DKIM and DMARC policies by creating an email sender with this domain.
For example:
- youcompany@talkbox.email
Custom Domain Option
TalkBox also offers a “custom domain” feature to customise the Sender – find out more
